Overview
In a distributed system, services are distributed among different systems and If a service is required to access another service over network, the most convenient way to authenticate is using password-based authentication schemas. In this approach, consuming service will passes the username and password over the network to get access to required services. It means serving services are required to maintain all the consumer credentials to validate each request. Same way consumer needs to maintain the credentials to consume the services.
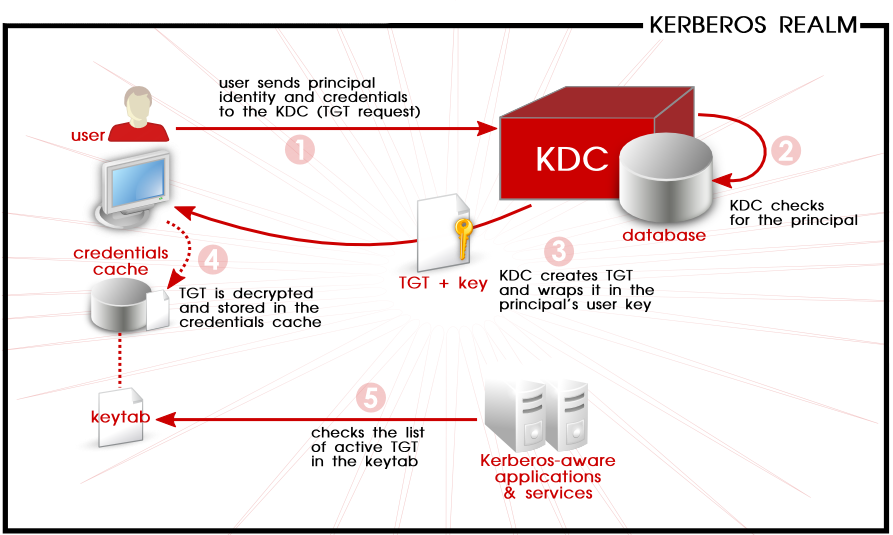
Kerberos is a computer network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner(source: wiki). Kerberos uses token with symmetric key cryptography. Kerberos can be used for Single Sign-0n where serving and consuming system are not required to maintain a separate set of credentials. Instead, they can use the network credentials which are used to login into the system. Kerberos protocol is supported by most of operating systems including Windows, Solaris, Unix and Unix-like OS. Refer wiki and Redhat to know how it works. There are few terms which we need to understand before it gets started.
- Key Distribution Center(KDC) is trusted third party system used to identity the system or user by principle and issues encrypted TGT(Ticket-Granting-Ticket) ticket.
- Authentication Server(AS) - an authentication system is part of KDC and used to validate the principle
- Ticket Granting Service(TGS) - once the principle is identity, KDC uses TGS to get the encrypted timestamped ticket(TGT)
Prerequisite
This article limits the scope of Kafka producer configuration using Spring Boot and not intended to explain about Kafka server admin configuration. Use Kafka quick start to have a kafka setup.
Kerberos configuration
-
Check if the consumer or provider system has Kerberos config file exist in a system. Use
locate or find command to search the file. Mostly you can find it in /etc/krb5
folder. If you find the file then skip to step 7.
$ find krb5.conf - If the file doesn't exist, create a folder krb5 in any path and then create
krb5.conf
with below configuration.
[libdefaults] default_realm = YOUR_REALM dns_lookup_kdc = false dns_lookup_realm = false ticket_lifetime = 86400 renew_lifetime = 604800 forwardable = true default_tgs_enctypes = rc4-hmac aes256-cts aes128-cts default_tkt_enctypes = rc4-hmac aes256-cts aes128-cts permitted_enctypes = rc4-hmac aes256-cts aes128-cts udp_preference_limit = 1 rdns = false kdc_timeout=10 [realms] YOUR_REALM = { kdc = YOUR_PRIMARY_KDC_SERVER_ADDRESS kdc = YOUR_SECONDARY_KDC_SERVER_ADDRESS admin_server = YOUR_KDC_ADMIN_SERVER_ADDRESS }In the above configuration, the capital bold letter needs to replace with your actual server and realm details. Other configurations like encryption algorithms ticket renew time or lifetime can adjust as you needed. Check with the infrastructure team if you are not sure of the above details. -
Create keytab file using ktutil command inside krb5 folder.
$ ktutilCommand prompt will change to ktutil - Add your principle, password and encryption algorithm
ktutil: addent -password -p YOUR_PRINCIPLE -k 1 -e rc4-hmacEnter a password when it prompts. -
Save the details into a keytab file
ktutil: wkt YOUR_FILE_NAME.keytab -
Quit from ktutil tools
ktutil: quit -
Initiate the login command to get the ticket and validate the configuration by using below
command.
$ kinitEnter the principle password when it prompts.
Spring configuration
Add kafka dependencies in spring boot pom.xml file.
Update application.yml with kafka configuration. Kafka service name should match with the Kafka server configuration. Replace your principle name keytab path accordingly.
Source code
Create a topic DATA.PRICE and start the Kafka server, Zookeeper and topic consumer before running the demo. Refer quick start for more information. Find the git for complete code. Please note that this code uses command prompt. Use com.techsams.spring.Application to run the program.